
Today The Official Merchant Services Blog is going to delve into the bigger picture of the impact that the Global Payments Data Breach is going to have on the payment processing industry. Obviously this news is going to have a huge impact on Global Payments itself. The company faces a big penalty after Visa dropped it from its registry of compliant service providers due to “unauthorized access into a portion of (Global Payments’) processing system.”
Fees and penalties related to reacquiring its compliance status and getting back on the registry will add up. In fact an executive from Co3 Systems, a data loss management firm, estimated the potential liability for a merchant with 1 million cards compromised could top $1.6 million from compliance fines alone. With Global’s own official statements indicating that the number of cards that were compromised being less than 1.5 million, the Co3 estimate is probably right in the ballpark of what Global faces.
The company also will take a hit to its business simply because of the breach itself and being dropped by Visa. While they are off the list, some potential customers may not be able to sign with them due to the lack of compliance status. And if the process to be reinstated takes too long, it could affect some of their current customers.
But there’s a larger context that needs to be considered with this data breach: PCI DSS itslef.
We’ve covered PCI Compliance very extensively in the blog. We looked at a report from Verizon last year that suggested 79% of organizations Verizon surveyed were found to be non-compliant in their initial audit in 2010. The study from the previous year had 78% of organizations were non-compliant. A study by Gartner Research demonstrated that 18% of merchants they surveyed were not PCI Compliant at all.
What is PCI?
These studies just underscore the large problem payment processing faces with security. The acronym PCI DSS stands for Payment Card Industry Data Security Standards. PCI Compliance is essentially the process of adhering to the standards set forth by the Payment Card Industry Data Security Standards Council (PCI DSS). You can review those standards in greater detail here. Essentially the standards are a set of requirements designed to ensure that all companies that process, store or transmit credit card information maintain a secure environment.
What’s the Problem?
One of the biggest criticisms of the PCI DSS is that it is the minimum agreed upon set of security protocols. Because of its nature as a consensus set of standards put together by the council, PCI is often criticized for being behind the curve or not being thorough enough to deal with the hackers who are trying to get at the data and breach the security of the transactions. Combine that with the studies that keep showing merchants are not keeping their compliance current or not even becoming compliant in the first place and you open the door for a lot of criticism against the system designed to keep transactions safe and secure.
Taylor Armerding wrote a compelling article for CSO Online on the issue of PCI compliance in the aftermath of the latest data breach. The lead statement of the article underscores the issue simply and effectively: “The latest data security breach to strike MasterCard and VISA has security experts focusing anew on the good and bad of PCI DSS. On one hand, the standard offers a clear blueprint on how to handle such a breach. On the other hand, compliance is usually not the cure, as this latest incident demonstrates.”
To add emphasis, Armerding quotes Neil Roiter, research director at Corero Network Security, as saying: “The Payment Card Industry Data Security Standard (PCI DSS) is highly prescriptive in nature, but simply complying does not ensure credit card security. Companies that rely on PCI DSS to solely dictate their security measures will continue to remain vulnerable to attack.”
The Weak Link
Armerding’s article suggested that compliance isn’t the be-all-end-all for security and that humans were still weakest link in the system. Quoting Anup Ghosh, founder and CEO of Invincea, a developer of browser protection systems, the article says that too much of the security standards are stuck in the past. Ghosh also suggests that PCI is complacent and easy for hackers to circumvent. Ghosh says that the systems in place are more designed to tell you what happened after the fact, being a reactive solution rather than a proactive solution. Ghosh then suggests that the data that was compromised was likely encrypted, but the security standards are behind the curve where it really counts: The Human Layer of Security.
Ghosh explains: “If I target employees, which is how you target these days, it is not very hard in phishing campaigns, to get employees to open an email or click on a link, which then provides access to their desktop and the privileges that come with it. [And in that case] Encryption is worthless.”
He then suggests a more proactive step of creating a more secure virtual environment for employees to work in so that whatever an employee clicks doesn’t end up compromising any data in the system.
PCI is Still Very Important
What Armerding and Ghosh say about PCI is quite compelling. But they both still point out that PCI Compliance is very important for merchants and payment processors. The standards may be behind the curve with the ever-clever hackers going after credit card data, but they set a starting point for security. They set the bar high enough that hackers have to put in work to circumvent the systems. Having PCI is so much better than not having it — which demonstrates how scary the Verizon and Gartner studies are.
Host Merchant Services advocates and performs a very zealous crusade for PCI Compliance. The company takes data security and safe transactions seriously and makes PCI Compliance a part of its value-added service package. HMS began a PCI Compliance Initiative last year that started with an ad campaign that offered for a limited time free PCI Compliance fees for merchants who signed up during that time. It then extended into an initiative run through a partnership agreement with HostMySite.com that offered a free PCI and Security Analysis to any customer interested, and now that same offer is available to anyone interested in Host Merchant Services, partnership or no partnership. The company provides on-call assistance with PCI Compliance questions and problems and will help all of its merchants get through the process with tips and advice from Host Merchant Services’ own PCI Compliance experts.
Tomorrow The Official Merchant Services Blog will follow up with the latest developments from the data breach, as well as more information about PCI Compliance, and PCI DSS issues that the payments industry and the tech industry are discussing.
For More Information
For more information about PCI Compliance, Host Merchant Services offers these resources:






 So there were definitely some differences in what was being reported by Krebs and being discussed, however grudgingly and tight-lipped, by Global in its official statements. It had gotten to a point of such discrepancy that Krebs was entertaining the idea that the
So there were definitely some differences in what was being reported by Krebs and being discussed, however grudgingly and tight-lipped, by Global in its official statements. It had gotten to a point of such discrepancy that Krebs was entertaining the idea that the 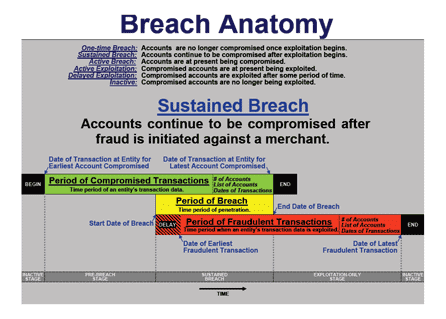



 After confirming the breach Garcia stated that the breach was “absolutely contained” and stated that there had been no “fraudulent transactions” related to the breach.
After confirming the breach Garcia stated that the breach was “absolutely contained” and stated that there had been no “fraudulent transactions” related to the breach.